



NOTICE

Recommendations for data protection
In order to minimize the risk of data security violations, we recommend the following organizational and technical actions for the system where your applications are running. Whenever possible, avoid exposing the PLC and control networks to open networks and the Internet. Use additional data link layers for protection, such as a VPN for remote access. Install firewall mechanisms. Restrict access to authorized persons. Use high-strength passwords. Change any default passwords regularly before and after commissioning.
Use the security features supported by CODESYS and the respective controller, such as encryption of communication with the controller and intentionally restricted user access.
For devices that support a device user management, the device editor includes the “Users and Groups” tab and the “Access Rights”. When offered by the device, you can view the user management for the device here as well as edit it in synchronization mode (not in online mode). Here, you can grant or deny specific permissions on the controller to the defined user groups.
The device user management can already be set up in the device description.
Note the commands in the “Online Security” menu. You can easily add, edit, or remove a user account on the controller where you are currently logged in.
In order for the “Access Rights” tab to be available in the device editor, the corresponding CODESYS option must be selected in the device editor and unlocked in the device description. If the device editor is not available, then contact the manufacturer of the controller.
In order to grant access rights to a user group, first the users and user groups have to be configured on the “Users and Groups” tab of the device editor. User management first has to be set up on the controller before access rights can be configured on it. In case the user management of a device is not enabled yet, it can be enabled in the following way: Either by switching to the synchronized mode on the “Users and Groups” tab, or by adding a new user by means of the command “Online Security Add Device User”.
General information about device user management
For the CODESYS Control devices, a user management is enforced by default.
Access rights can be granted to groups only, not individual users. Therefore every user has to be a member of a group.
Access rights can be granted for the following actions which are executed on the individual objects of the controller:
-
Add/Remove
-
Modify
-
View
-
Execute
An object on the controller is usually assigned to just one controller component.
Each object can use all of the listed actions, but usually only the permissions for the following actions are needed on an object:
-
“View”
-
“Modify”
The objects are organized in a tree structure. There are two root objects for the two kinds of objects:
-
“Runtime objects Device”: In these objects, all objects are managed that have online access in the controller and therefore have to control the access rights.
-
“File system objects /”: In these objects, the permissions can be granted to folders of the current execution directory of the controller.
The child objects inherit the access rights from the root object (also “Device” or "“/”"). If a permission of a user group is denied or explicitly granted to a parent object, then this affects all child objects.
A single permission can be explicitly granted or denied (green plus sign or red minus sign), or remain "neutral" (light gray character). Neutral means that the permission has been neither explicitly granted nor denied. In this case, the permission of the parent object applies.
If no permission has been explicitly granted or denied in the entire hierarchy of the object, then it is by definition denied. As a result, all permissions are initially denied (exception: the access right for the “View” action). Initially, this permission is explicitly granted for every user group both on the “Device” runtime object as well as on the "“/”" file system object. This allows read access to all objects, unless it is explicitly denied in child objects.
For an overview table for the objects, see the "Tab 'Access Rights'" chapter.
See the following instructions for handling the editor for the device user management:
First-time login on the controller in order to edit or view its user management
Requirement: The connection to the controller is configured. The controller supports a device user management, but one is not active yet.
-
Double-click the controller device object in the device tree.
The device editor opens.
-
Click the “Users and Groups” tab.
-
Click
 .
.A dialog opens prompting whether the device user management should be activated.
-
Click “Yes” to acknowledge the dialog prompt.
The “Add Device User” dialog opens.
-
Now create a device user in order to edit the user management as this user. In this case, only the “Administrator” group is available. Specify a “Name” and “Password” for the user. The password strength is displayed. Note also the set options regarding a password change. By default, the password can be changed by the user at any time. Click “OK” to confirm.
The “Device User Logon” dialog opens.
-
Specify a “User name” and “Password” for the user who you just defined.
After you click “OK” to confirm, the device user management is displayed in the editor view. It contains the user of the administrator group who you just defined. The name of this user is also displayed in the taskbar of the window as “Device User”.
Setting up a new user in the user management of the controller
Requirement: The controller has a device user management. You have the corresponding access data.
-
Double-click the controller device object in the device tree.
The device editor opens.
-
Click the “Users and Groups” tab.
-
Click
 (Synchronization) to load the user management configuration from the controller to
the editor. If you are not logged in to the device yet, then the “Device User Logon” dialog opens for entering the user name and password.
(Synchronization) to load the user management configuration from the controller to
the editor. If you are not logged in to the device yet, then the “Device User Logon” dialog opens for entering the user name and password.The user management configuration of the device is shown in the editor.
-
In the “Users” view, click “Add”.
The “Add User” dialog opens.
-
Specify the name of the new user and assign the user to a group. This counts as the user's minimum required default group. The user can be assigned to other groups later. Define and confirm a “Password” for the user. Define whether the user can change the password and whether the user has to change the password at the first login. Click “OK” to confirm.
The new user appears in the “Users” view as a new node and in the “Groups” view as a new subentry of the selected default group.
Changing of access rights to controller objects in the user management of the controller
Requirement: The controller has a device user management. You have the corresponding access data.
-
Double-click the controller device object in the device tree.
The device editor opens.
-
Click the “Access Rights” tab.
-
Click
 (Synchronization) to load the rights management configuration from the controller
to the editor. If you are not logged in to the device yet, then the “Device User Logon” dialog opens for entering the access data.
(Synchronization) to load the rights management configuration from the controller
to the editor. If you are not logged in to the device yet, then the “Device User Logon” dialog opens for entering the access data.The access rights management configuration of the device is shown in the editor.
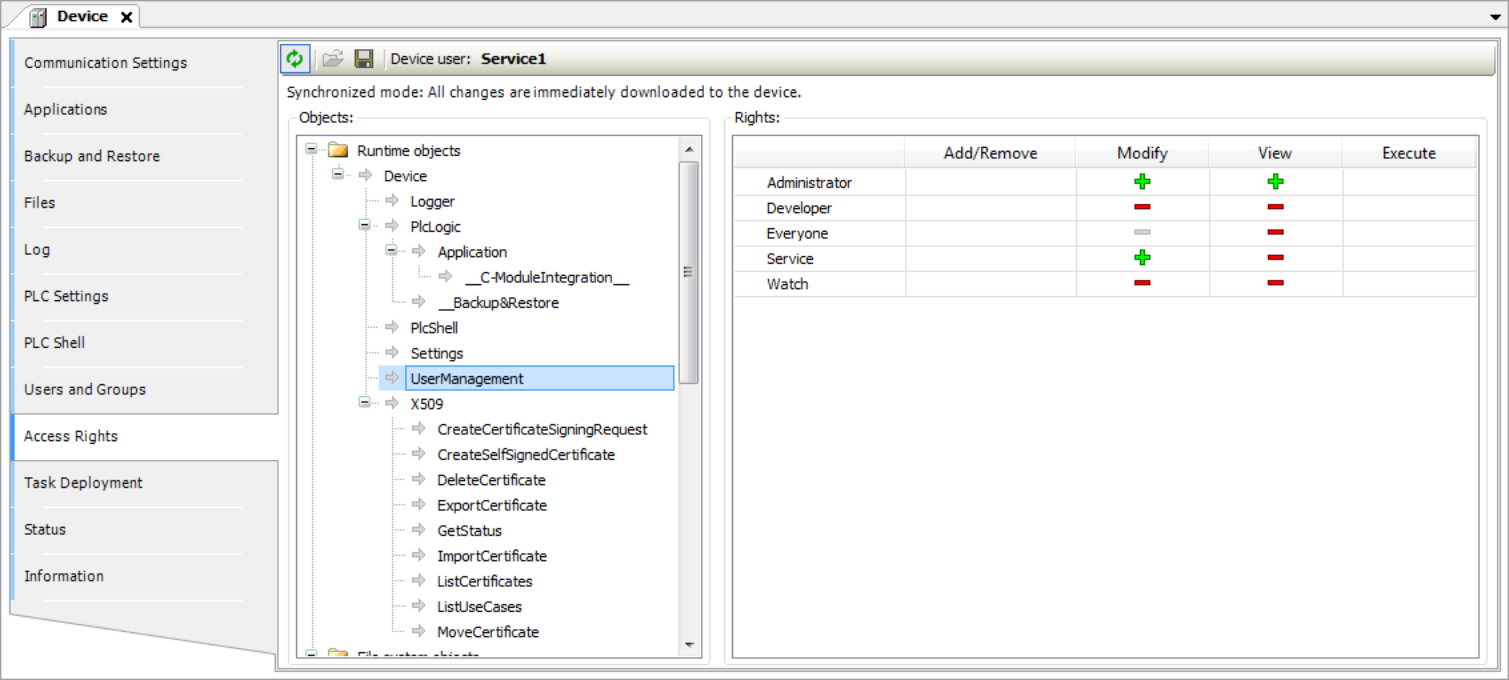
-
Select the object whose access right you want to change to the left in the object tree.
In the “Rights” view, a table shows the access rights to this object for all configured user groups.
-
Double-click the right in the table that you want to change.
If the object has child objects, then a dialog prompts whether you want to modify the permissions for the child objects.
-
Click “Yes” or “No” to close the prompt.
The permissions are switched from "allowed"
 to "not allowed"
to "not allowed"  , or the other way around. The symbol in the table cell changes accordingly. Explicitly
set permissions appear in the table as green or red symbols. Rights that are inherited
from a parent object appear as gray symbols.
, or the other way around. The symbol in the table cell changes accordingly. Explicitly
set permissions appear in the table as green or red symbols. Rights that are inherited
from a parent object appear as gray symbols.
Transferring and enabling a saved user management in offline mode from a DUM2 file to a controller
In V3.5 SP16 and higher, a file (*.dum2) to be encrypted with a password is used for exporting a user management.
-
Double-click the controller device object in the device tree.
The device editor opens.
-
Click the “Users and Groups” tab.
-
Click
 .
. The dialog for selecting a file from the local file system opens.
-
Select the file (
<file name>.dum2) with the desired user management from the local file system and click “Open” to confirm.The “Enter Password” dialog opens.
-
Specify the password that was assigned when the user management file was exported (possible by means of the
 button).
button).CAUTION: The import of a device user management by means of a
*.dum2file completely overwrites the existing user management on the device. In order to log in to the device again afterwards, you need authentication data from the recently imported user management.When the password is entered correctly, the configuration from the downloaded user management file is now displayed in the editor view.
-
Edit the configuration however you like. For example, change the user password or add a new user.
Every change is downloaded immediately to the device.
See also
Configuring the password policy and login lock
You can configure a password policy and login lock for the runtime system. Using these two mechanisms makes sure that the credentials configured for the controller are as secure as possible and that attackers cannot guess the credential by repeated attempts. By default, a password policy is not enabled. The login lock is enabled by default for the administrator user group because this user group needs to fulfill increased security criteria and should also be better protected. When the maximum number of login attempts has been exceeded, the user will be locked out for the configured amount of time (3600 seconds by default).
Unlocking a locked user
The following options are available for unlocking a user who has been locked for a specific period of time:
-
An administrator or a member of a user group with write permission for the user group of the locked user assigns a new password for the user.
-
The runtime system is restarted.
Enabling and changing a password policy
-
In the device tree, double-click the controller.
The device editor opens. The “Communication Settings” tab is displayed.
-
In the header, click the “Scan Network” button, and in the “Select Device” dialog, select the desired device. Then click “OK”.
The active path to the controller is set.
-
In the “Device” menu, select “Change Runtime System Password Policy”.
-
In the “Change Runtime System Password Policy” dialog, select the “Password policy is active” option.
The password policy with the displayed password settings is enabled.
The detailed default password settings can be found in the description of the dialog.
-
Change individual password settings as needed.
-
Click “OK” to confirm the changes made.
The configured password policy is immediately applied when creating a new user and when changing the password for an existing user. Only new passwords which fulfill the password policy can be created.
Configuring a login lock
-
In the device tree, double-click the controller.
The device editor opens. The “Communication Settings” tab is displayed.
-
In the header, click the “Scan Network” button, and in the “Select Device” dialog, select the desired device. Then click “OK”.
The active path to the controller is set.
-
In the “Device” menu, select “Change Runtime System Password Policy”.
-
In the “Change Runtime System Password Policy” dialog, you can change the default settings for the login lock or disable the login lock.
-
Click “OK” to confirm the changes made.
The configured login lock is immediately applied when logging in to the device user management for users of the user group selected in the “Scope”.
When the number of login attempts specified in the “Maximal Retries” field is exceeded, the user will be locked out for the amount of time which is specified in the “Lock duration” field.






