The controller must be located in a protected environment in order to avoid accidental or intended access to the controller or the application.
A protected environment can be:
-
Locked control cabinets without connection from outside.
-
No direct internet connection.
-
Use firewalls and VPN to separate different networks.
-
Separate different production areas with different access controls.
To increase security, physical access protection measures such as fences, turnstiles, cameras or card readers can be added.
Follow these rules for the protected environment:
-
Keep the trusted network as small as possible and independent from other networks.
-
Protect the cross-communication of controllers and the communication between controllers and field devices via standard communication protocols (fieldbus systems) using appropriate measures.
-
Protect such networks from unauthorized physical access.
-
Use fieldbus systems only in protected environments. They are not protected by additional measures, such as encryption. Open physical or data access to fieldbus systems and their components is a serious security risk.
-
Physically protect all equipment, i.e., ensure that physical access to computers, network equipment and cables, controllers, I/O systems, power supplies, etc., is limited to authorized persons
-
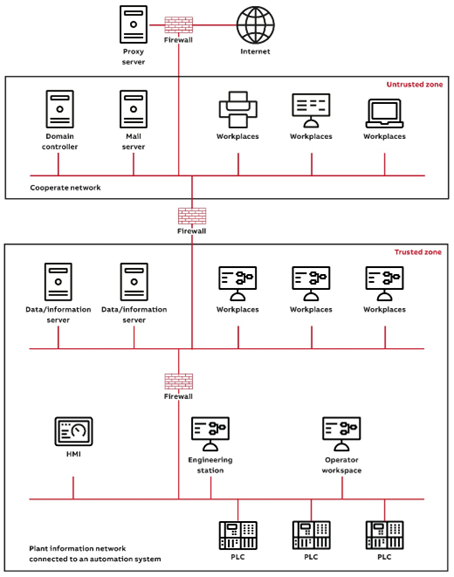
When connecting a trusted network zone to outer networks, make sure that all connections are through properly configured secure interconnections only, such as a firewall or a system of firewalls, which is configured for “deny by default”, i.e., blocks everything except traffic that is explicitly needed to fulfill operational requirements.
-
Allow only authorized users to log on to the system, and enforce strong passwords that are changed regularly.
-
Continuously maintain the definitions of authorized users, user groups, and access rights, to properly reflect the current authorities and responsibilities of all individuals at all times. Users should not have more privileges than they need to do their job.
-
Do not use the system for e-mail, instant messaging, or internet browsing. Use separate computers and networks for these functions if they are needed.
-
Do not allow installation of any unauthorized software in the system.
-
Restrict temporary connection of portable computers, USB memory sticks and other removable data carriers. Computers that can be physically accessed by regular users should have ports for removable data carriers disabled.
-
If portable computers need to be connected, e.g., for service or maintenance purposes, they should be carefully scanned for viruses immediately before connection.
-
All CDs, DVDs, USB memory sticks and other removable data carriers, and files with software or software updates, should also be checked for viruses before being introduced into the trusted zone.
-
Continuously monitor the system for intrusion attempts.
-
Define and maintain plans for incident response, including how to recover from potential disasters.
-
Regularly review the organization as well as technical systems and installations with respect to compliance with security policies, procedures and practices.
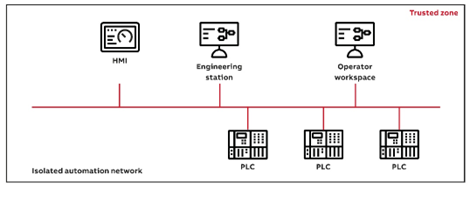
A protected local control cabinet could look like in figure 255. This network is not connected to any external network. Security is primarily a matter of physically protecting the automation system and preventing unauthorized users from accessing the system and from connecting or installing unauthorized hardware and software.
A protected local control cabinet could look like in the picture below. This network is not connected to any external network. Security is primarily a matter of physically protecting the automation system and preventing unauthorized users from accessing the system and from connecting or installing un-authorized hardware and software.
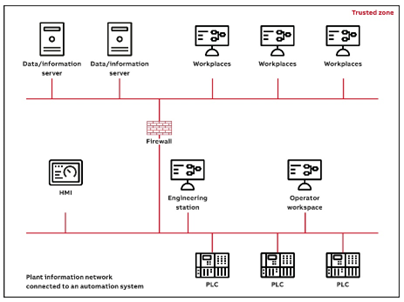
Servers and workplaces that are not directly involved in the control and monitoring of the process should preferably be connected to a subnet that is separated from the automation system network by means of a router/firewall. This makes it possible to better control the network load and to limit access to certain servers on the automation system network. Note that servers and workplaces on this subnet are part of the trusted zone and thus need to be subject to the same security precautions as the nodes on the automation system network.
For the purposes of process control security, a general-purpose information system (IS) network should not be considered a trusted network, not the least since such networks are normally further connected to the Internet or other external networks. The IS network is therefore a different lower-security zone, and it should be separated from the automation system by means of a firewall. The IS and automation system networks should form separate domains.