|
“Runtime objects Device” |
||||||
|
|
Online access to the logger is read only. Therefore, only the “View” access right can be granted or denied here. |
|||||
|
|
All IEC applications are inserted here automatically as child objects during download. When an application is deleted, it is removed automatically. This allows specific control of online access to the application. Access rights can be assigned centrally over all applications in the “PlcLogic” The “Administrator” and “Developer” user groups have full access to the IEC applications. The “Service” and “Watch” user groups only have read access (for example for read-only monitoring of values). |
|||||
|
The following table shows which action is affected in particular when a specific access right is granted for an IEC application. x : The permission has to be set explicitly. -: The permission is not relevant. |
||||||
|
|
Operation |
Permission |
||||
|
“Add/Remove” |
“Execute” |
“Modify” |
“View” |
|||
|
Login |
|
|
|
|
||
|
Create |
|
|
|
|
||
|
Create child object |
|
|
|
|
||
|
Delete |
|
|
|
|
||
|
Download / online change |
|
|
|
|
||
|
Create Boot Application |
|
|
|
|
||
|
Read variable |
|
|
|
|
||
|
Write Variable |
|
|
|
|
||
|
Force Variable |
|
|
|
|
||
|
Set and delete breakpoint |
|
|
|
|
||
|
Set Next Statement |
|
|
|
|
||
|
Read call stack |
|
|
|
|
||
|
Single Cycle |
|
|
|
|
||
|
Switch on flow control |
|
|
|
|
||
|
Start / Stop |
|
|
|
|
||
|
Reset |
|
|
|
|
||
|
Restore retain variables |
|
|
|
|
||
|
Save retain variables |
|
|
|
|
||
|
|
Only the “Modify” permission is evaluated at this time. This means that only when the “Modify” permission has been granted to a user group can PLC shell commands also be evaluated. |
|||||
|
|
Additional external connections to the controller can be configured below this node. Currently, access to the OPCUA server can be configured here. |
|||||
|
|
This is the online access to the configuration settings of a controller. By default, access to “Modify” is granted only to the administrator. |
|||||
|
|
This is the online access to the user management of a controller. By default, read/write access is granted only to the administrator. 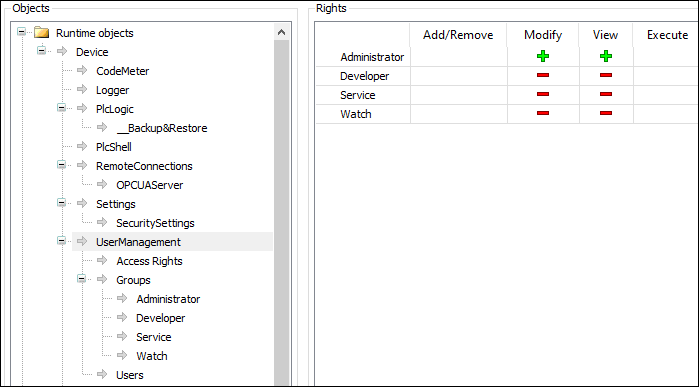
For more information see: ⮫ “Handling of Device User Management ” |
|||||
|
|
This controls the online access to the X.509 certificates. Two types of access are distinguished here:
Every operation is assigned to one of these two access rights. Each operation is inserted as a child object below X509. Therefore, access per operation can now be fine-tuned even more. |
|||||
|
“File system objects /” |
||||||
|
All folders from the execution path of the controller are inserted below the "“/”" file system object. This allows you to grant specific rights to each folder of the file system. |
||||||





